ThreatConnect Intelligence Requirements
The ThreatConnect Intelligence Requirements capability enables CTI analysts and their customers to more efficiently prioritize the most critical threats. It centrally captures and implements threat intelligence requirements (IRs) directly in the TI Ops Platform, including IRs, PIRs, SIR’s, RFIs and RRs. Intelligence Requirements makes threat intelligence more accessible and actionable for cybersecurity teams.

From Undocumented to Documented, Actionable Intel Requirements
We empower CTI stakeholders, like SOC and vulnerability management teams, to clearly communicate their threat intel data needs to CTI teams. Through Intelligence Requirements, CTI teams can generate and disseminate the appropriate type of threat intel to their customers to help them proactively respond to the most high-impact business threats.
Read Intelligence Requirements DatasheetFrom Overwhelming Workload to Efficient Management
Tracking IRs in the TI Ops platform accelerates workflow by speeding up data collection and aggregation, reducing the need for external research. Additionally, this increases uniformity in threat analysis and response, reducing the risk of discrepancies among security analysts.
Watch How to Streamline Your Cyber Threat Research with ThreatConnect Intelligence Requirements WebinarFrom Spreadsheets to Shared, Accessible Requirements
Intelligence Requirements provides a robust capability to capture and enable your IRs in one place and maximize the Planning and Direction phase with the rest of your organization. Intelligence Requirements are easy to set up, manage, and optimize, decreasing reliance on wikis, docs, and spreadsheets.
Create Intelligence Requirements in 5 Easy StepsThreatConnect Advantages
Organize Diverse Requirements
Simplify the management of a wide array of intelligence requirements, from Intelligence Requirements to Research Requests. The Intelligence Requirements capability in the ThreatConnect Platform enables CTI teams to centrally collect, manage, and operationalize a range of requirements, like Priority Intelligence Requirements (PIRs) and Specific Intelligence Requirements (SIRs). This approach transforms intelligence management into a seamless, tailored experience, boosting organization and efficiency.
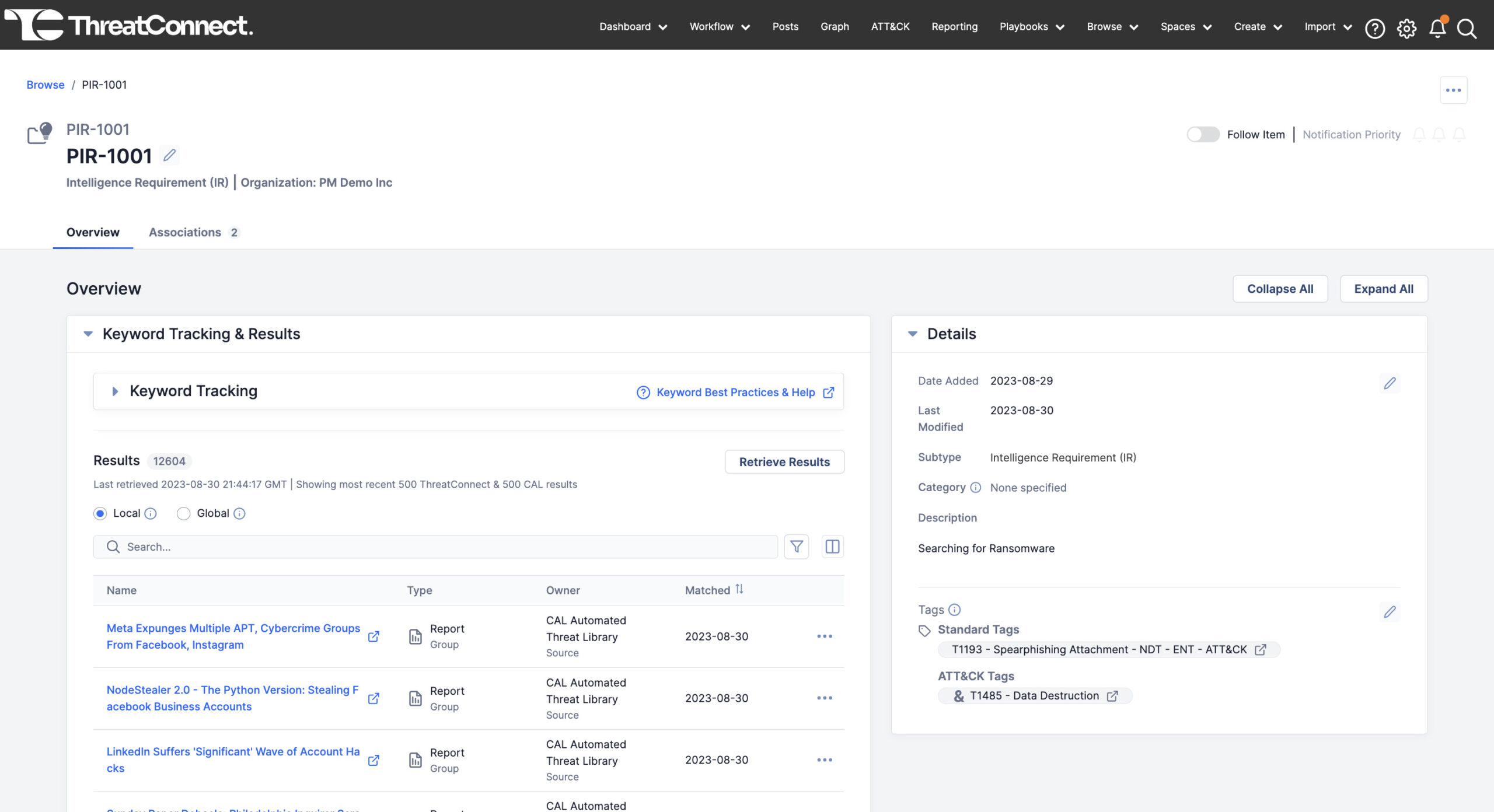
Automated OpenSearch Retrieves Relevant Information
Automated OpenSearch is engineered to quickly identify relevant data in ThreatConnect aligned with your requirements. It monitors on-demand and at daily intervals, ensuring a constant flow of up-to-date data. All your intel requirement-related data is automatically updated in the Intelligence Requirements’ details page.
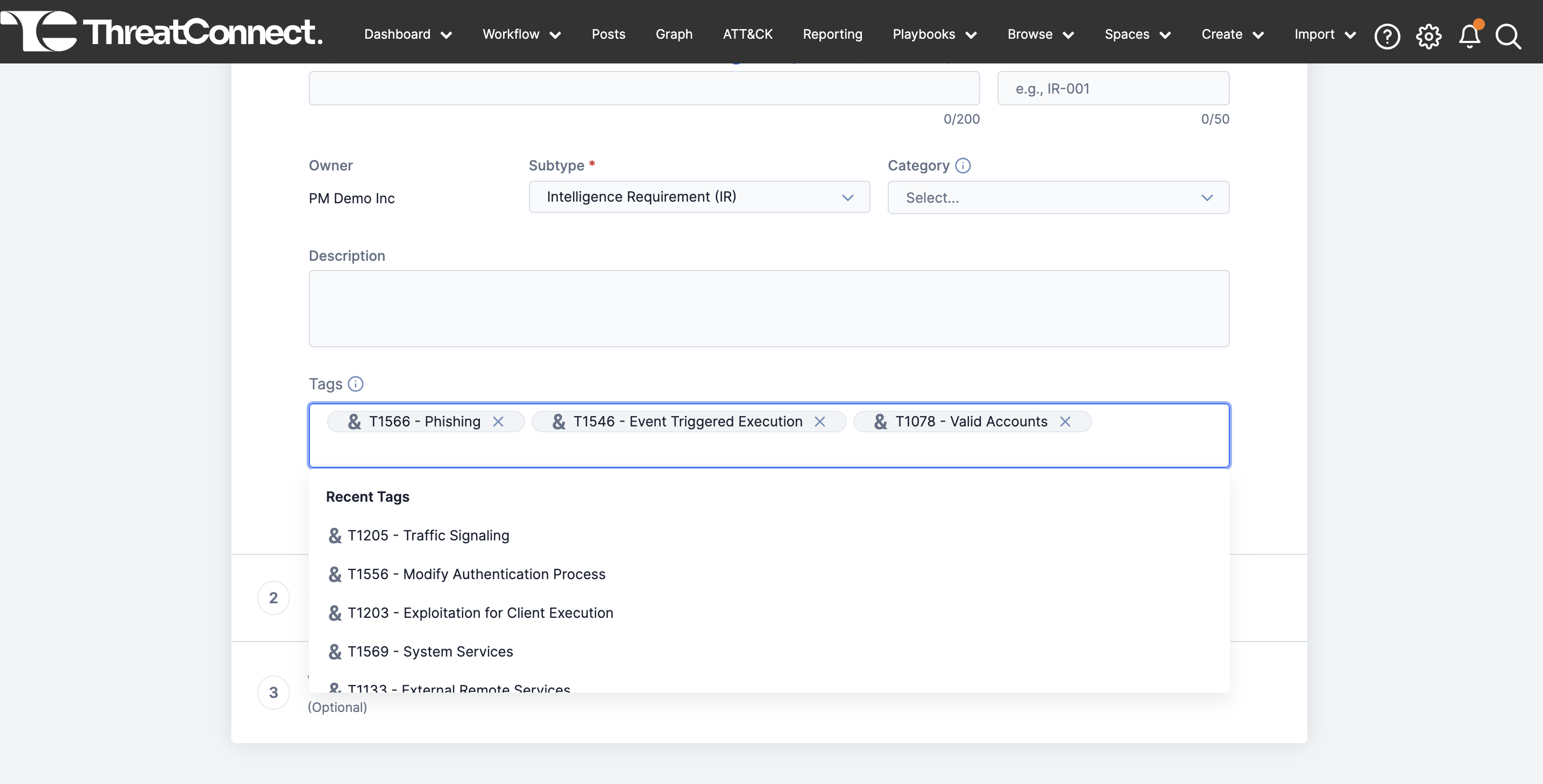
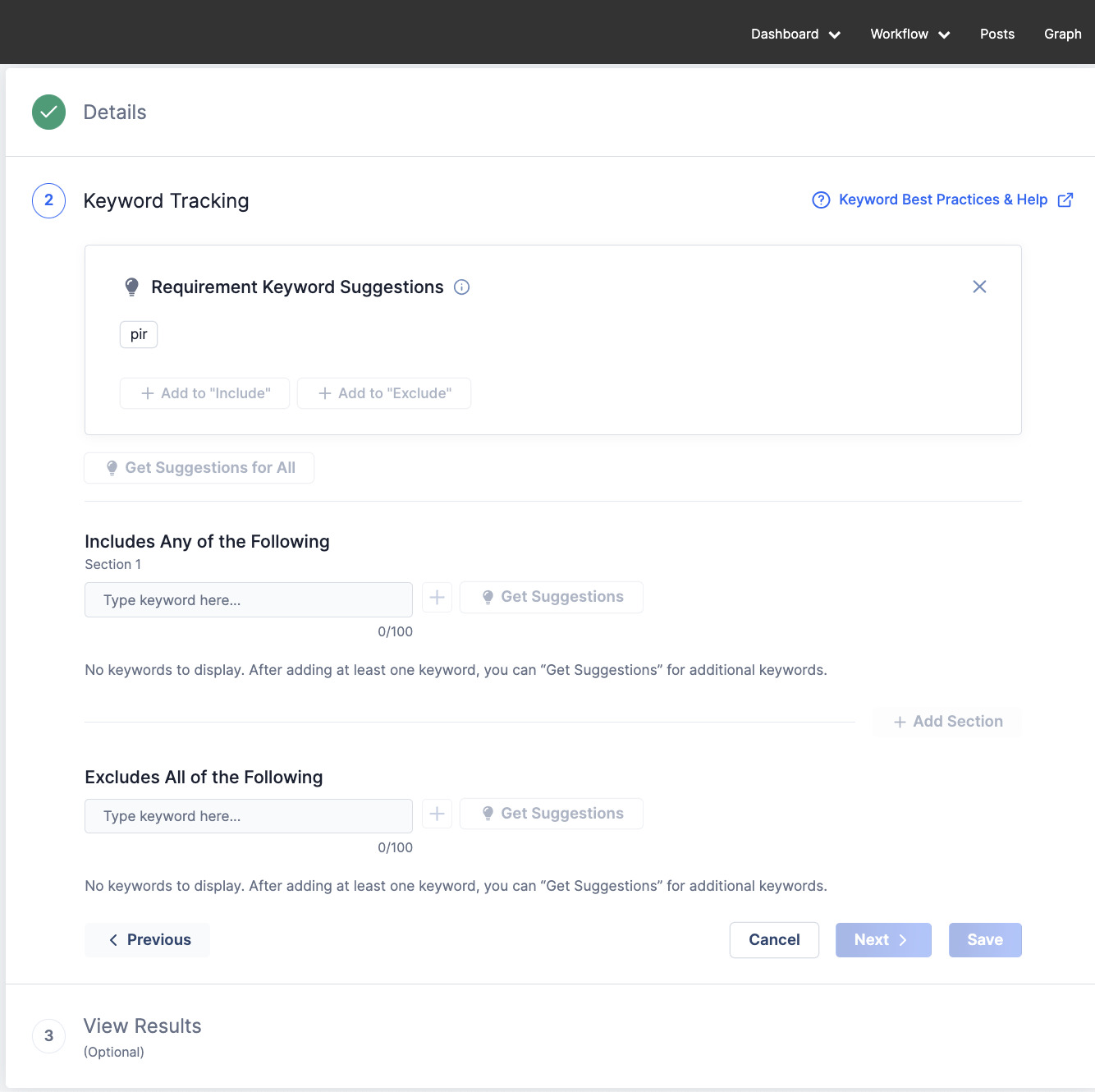
Easy-to-Use Keyword Tracking
With the keyword query feature in Intelligence Requirements, you can easily select from suggested standard and ATT&CK tags, generated from your keywords, giving you the option to include or exclude them as needed. This flexibility ensures precise and efficient searches tailored to your requirements.
Ready to Enhance Your Cybersecurity?